Own the data, disown the risk
We often speak to companies who are rightfully weary about how to store their most sensitive customer data. At the same time, companies want access to valuable customer data they need to provide services. Insert Footprint: a platform built to allow you to securely store user data with peace of mind, but have access to it when needed. Our value proposition of combining KYC with Security becomes increasingly clear when we describe our vaulting infrastructure based on strong cryptography and Nitro Enclaves, our granular attribute-level Identity and Access Management (IAM) features, and of course an immutable security event log. Footprint answers a question facing all decision-makers on what used to be a trade-off: how can I not just vault new data efficiently, but also use and transmit it where it needs to go.
Enter the Vault Proxy
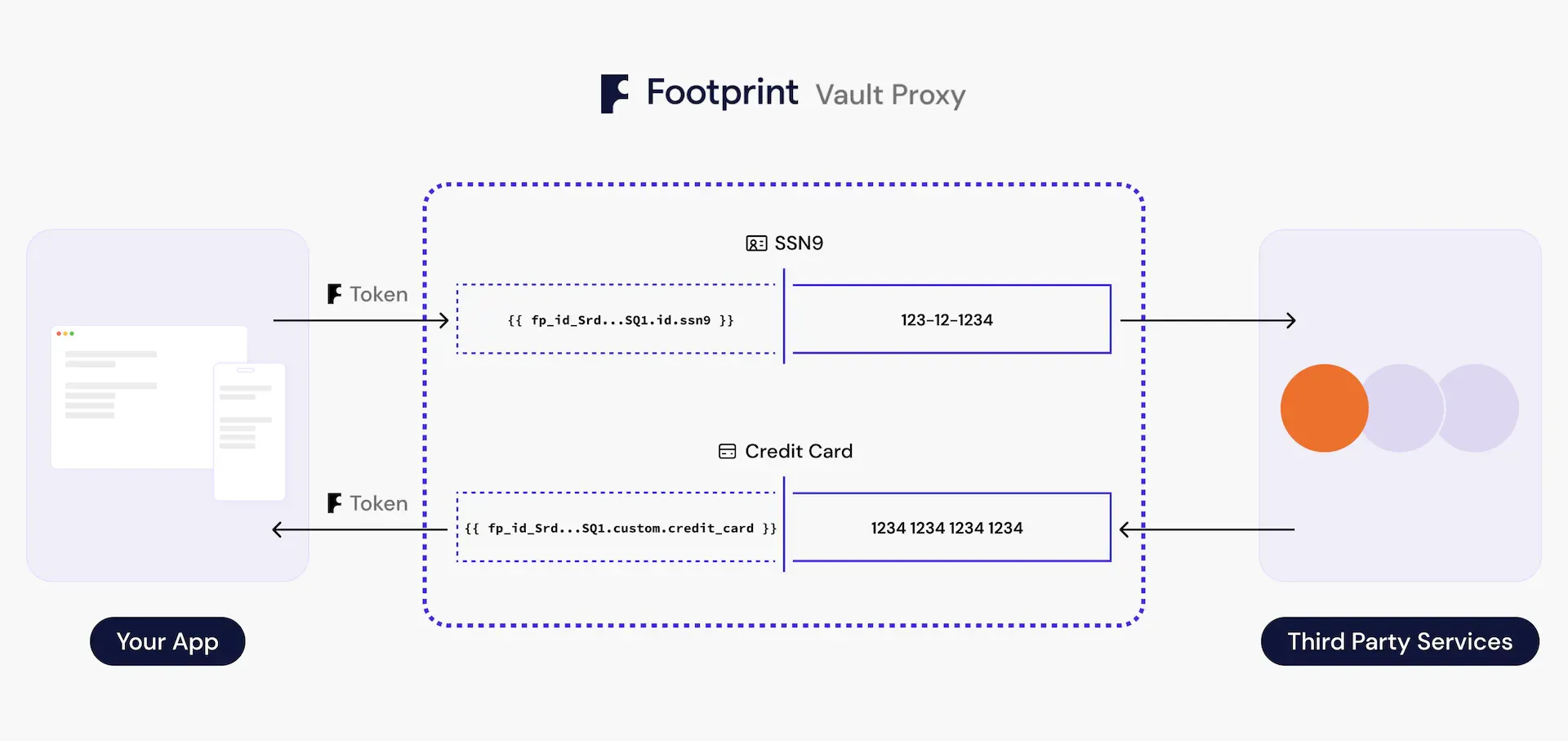
We built our Vault Proxy to answer this gnarly problem of sharing data securely at scale. The Vault Proxy is built to send and receive data in a secure and auditable way. We believe sharing data is not the enemy, and it is no longer optional for most businesses — our mission at Footprint is to bring this trust all the way from the user experience to the inner decisioning and processing systems of third party banking providers.
At a high level, our Vault Proxy aims to make it easy to accomplish 3 things:
- Never handle sensitive data outside of secure, compliant environments (like our Enclave-based vaults or our embedded components)
- Easily share data to third party services you run your business on: payment processors, card issuers, additional decision engines, auditing and reporting, etc.
- Ingest and vault sensitive data before it ever touches your applications or infrastructure, keeping your systems out of scope for security need
If we can accomplish these three goals, we believe your business will secure its most important assets. You can focus on the more pressing needs that your customers have, and not worry about compliance, risk, and security.
Getting technical
In the simplest form, the Vault Proxy is a proxy server with special powers. Just like any proxy server: you send a request to it and expect it to forward that request to some destination. What makes our proxy special, however, is that you can send data identifiers or tokens instead of sensitive data, and the Vault Proxy can “hydrate” the request — in flight, in a secure environment — with the actual sensitive data. We call this Egress detokenization.
What’s even more powerful is that often you may also need to consume and receive sensitive data (like a card number that you are issuing for a customer), and the Vault Proxy can do exactly this. We call this Ingress tokenization — the process of “dehydrating” sensitive data from the response that comes back from the destination server and vaulting the sensitive data, replacing it with tokens in place.
Let’s look at a live example. Acme wants to issue a debit card for a customer from CardService but first Acme needs to send some KYC data to their banking partner.
Below you can see what the request and response would look like, no sensitive data in plaintext:
#
# Acme => Footprint (proxy request)
#
curl \
-u 'sk_test_CXUs...:' \
-H 'x-fp-proxy-footprint-token: fp_id_Zfd...' \
https://api.onefootprint.com/proxy/proxy_id_AY5e... \
--data \
'{\
"name": "{{ id.first_name }} {{ id.last_name }}",\
"full_ssn": "{{ id.ssn9 }}",\
"zip_code": "{{ id.zip_code }}",\
}'
#
# Acme <= Footprint (proxy response)
#
{
"success": true,
"error": null,
"total_cards": 4,
"new_card": {
"pan": "{{ card.number }}",
"security_code": "{{ card.cvc }}",
"expiration": "{{ card.exp_month }}/{{ credit_card.exp_year }}",
}
}
But behind the scenes, the Vault Proxy is decrypting and tokenizing sensitive data in its secure environment.
Egress detokenization
In this step, the Vault Proxy parses the incoming request, extracts tokens (i.e. {{ fp_id_xyz.id.ssn9 }}), finds and decrypts the encrypted data referenced by the tokens, hydrates the request by substituting the underlying plaintext for the tokens, and finally sending the hydrated request to the proxy destination.
Ingress tokenization
In the last step, the Vault Proxy parses the response from the proxy destination, extracts and encrypts data to vault (i.e. specified via config using an JSONPath/XPath like selector assignment fp_id_xyz.credit_card.number=$.new_card.pan), dehydrates the response by substituting the newly vaulted plaintext with corresponding tokens, i.e. {{ fp_id_xyz.credit_card.number }}.
Unified configuration, secrets, and secure connections
Vault Proxy destinations are some of your most important third party services — this is where you send and receive highly sensitive data to/from — and Footprint’s Vault Proxy Configurations elevate security and the developer experience so you can safely and easily route sensitive data to your partners.
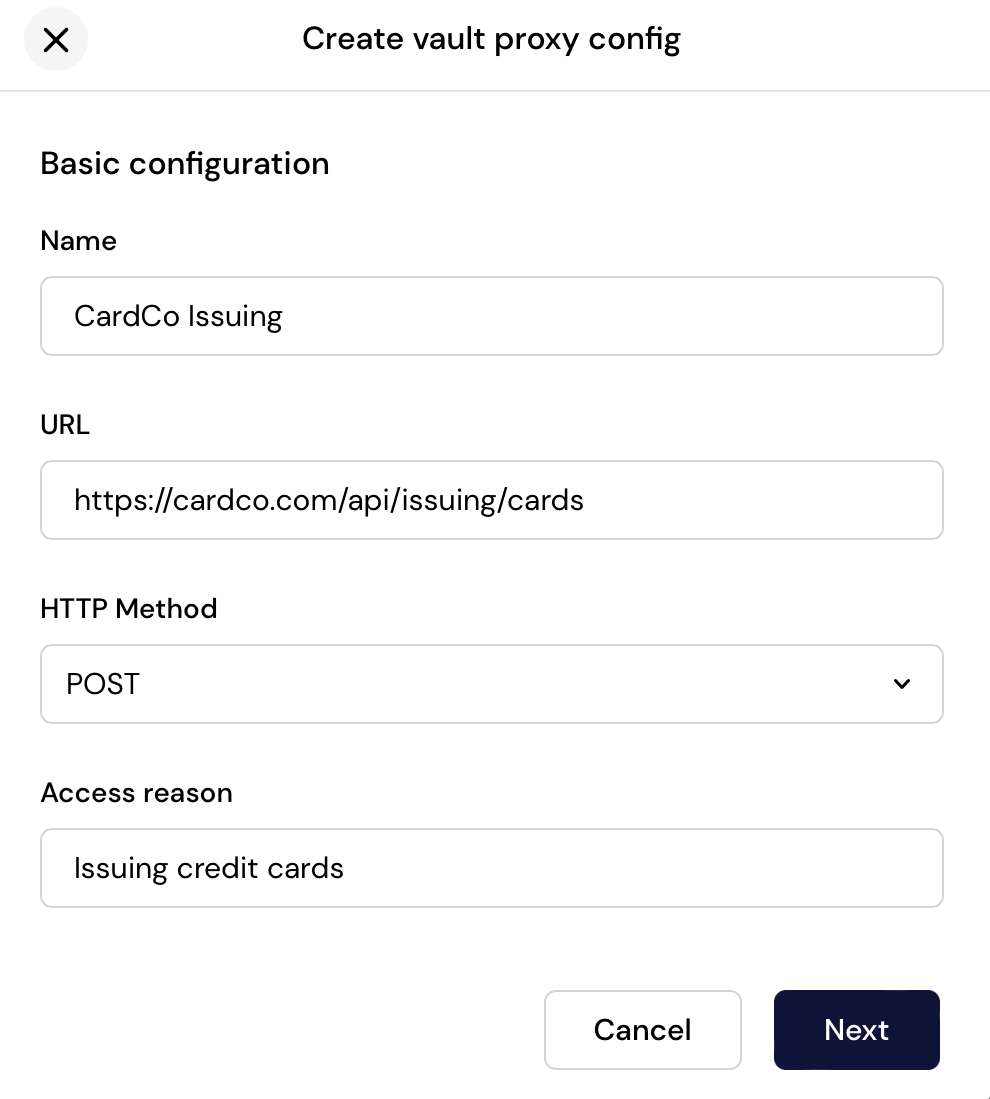
Basic configuration and secrets
Either in code or using our developer dashboard, configure your proxy destination: URL, HTTP verb, and even the access reason make audit logs more manageable. You can configure headers and API keys (secret headers) to reduce the surface area and scope of API secrets in your code base. Secrets like API Keys leverage the same Nitro Enclave-based vaulting infrastructure.
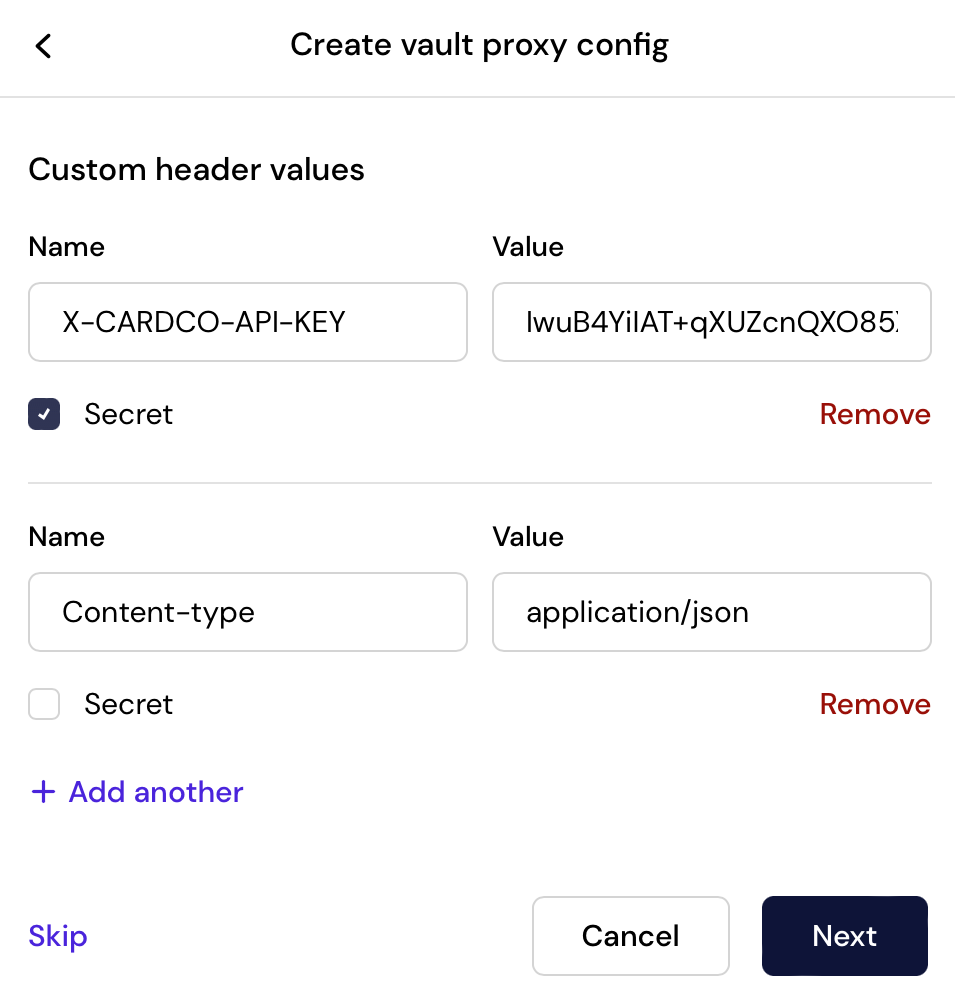
Secure your connections to third parties
One of the complexities of working in regulating spaces, like financial technology, is that banking partners and card processors have stringent requirements on authentication schemes and connections into their networks. For example: some partners we’ve seen require mutual TLS certificate based authentication, whitelisted IP addresses, and even pinning a custom Root Certificate Authority to securely negotiate a TLS connection.
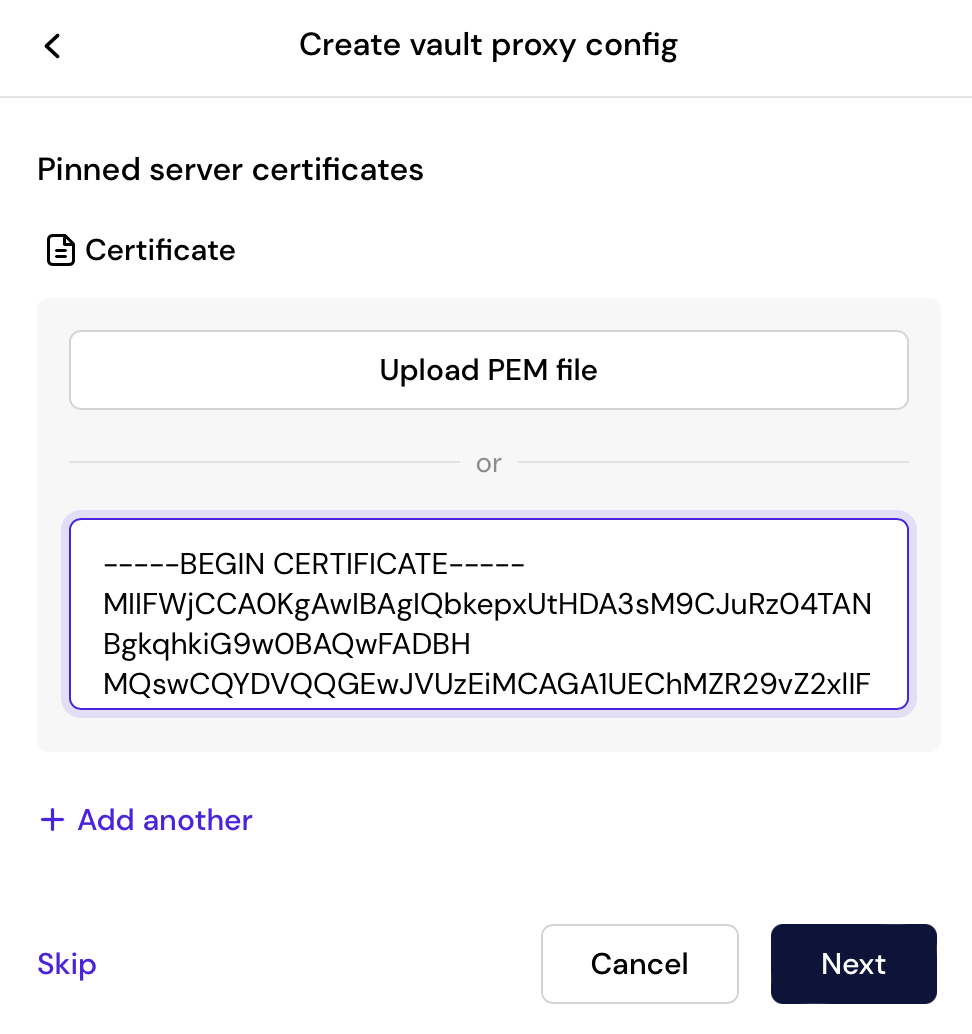
Footprint simplifies and secures how you can interface with your most important services. You can use Footprint’s Vault Proxy configuration to manage your client certificates, install server certificates with custom Root CAs, and most importantly manage client private keys using the same Nitro Enclave based vaulting infrastructure. Updating certificates and keys becomes a breeze, and requires no code changes.
Built in access control
While the Vault Proxy is special in some ways, in its simplest form it’s a way to decrypt data. Footprint’s platform has built in Identity and Access management, that makes it easy to limit and control who can decrypt what data attributes — and this fully extends to invoking the Vault Proxy. Easily control permissions on API keys and limit the data that specific micro-services, applications, or code have decryption capabilities.
Onboarding, KYC, and KYB
It’s worth mentioning that the Vault Proxy is designed to work seamlessly with Footprint’s KYC and KYB onboarding flows. This means you can offload all of the risk of collecting data, storing it, and sending it to third party banking, decisioning, and payment partners all while removing your own risk, security, and compliance headache.
Where to next?
Learn more by reading our Vault Proxy Documentation.